Configure Kerberos Constrained Delegation (Optional)
If either of these scenarios is true in your environment, you will need to configure Kerberos delegation to the CAs from the Keyfactor Command server hosting the Keyfactor Command Management Portal:
- You wish to use the option in Keyfactor Command to allow interactions with the CA
 A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. via the Keyfactor Command Management Portal (e.g. certificate approval or revocation) to be done in the context of the user logged into the Keyfactor Command Management Portal rather than in the context of the Keyfactor Command service account under which the application pool is running or an explicit user configured in the CA configuration within Keyfactor Command.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. via the Keyfactor Command Management Portal (e.g. certificate approval or revocation) to be done in the context of the user logged into the Keyfactor Command Management Portal rather than in the context of the Keyfactor Command service account under which the application pool is running or an explicit user configured in the CA configuration within Keyfactor Command. - You wish to enroll for certificates through the Keyfactor Command Management Portal after authenticating to the portal using Kerberos authentication rather than Basic authentication. If you wish to use the Keyfactor Command Management Portal but don’t wish to configure delegation or an explicit user configured in the CA configuration within Keyfactor Command, you will need to set the Keyfactor Command Management Portal to support Basic authentication only.
Configuring Kerberos delegation in Active Directory allows the user’s Kerberos credentials to be delegated from the Keyfactor Command server to the CA(s) to allow the Keyfactor Command server to act on behalf of the user.
The types of interactions affected by delegation in the Keyfactor Command Management Portal include:
- Enrollment
 Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). for certificates
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). for certificates - Approval of pending certificate requests
- Denial of pending certificate requests
- Revocation of certificates
- Certificate key recovery
There are two different approaches to configuring constrained delegation:
- With the traditional version of constrained delegation, you configure the service account under which the Keyfactor Command application pool runs and the machine account of the Keyfactor Command server to be allowed to delegate to each of your CAs.
- With the newer resource-based constrained delegation introduced in Windows server 2012, you configure each of your CAs to be allowed to receive delegation from the service account under which the Keyfactor Command application pool runs and the machine account of the Keyfactor Command server. This option requires at least one domain controller that's server 2012 or better, though there can be 2008 or 2008 R2 domain controllers in the mix.
With both approaches to constrained delegation, you need to set the service principal name (SPN) for the Keyfactor Command server (see Configure the Service Principal Name for the Keyfactor Command Server).
To configure Kerberos constrained delegation on the machine account of the Keyfactor Command server:
- Open Active Directory Users and Computers and browse to locate the machine account of the Keyfactor Command server and open its properties.
- On the Delegation tab for the machine account, choose "Trust the computer for delegation to specified services only" and under that "Use any authentication protocol" and then click Add.
- In the Add Services dialog, click Users or Computers and browse to locate the computer account for one of the CAs to which you wish to delegate.
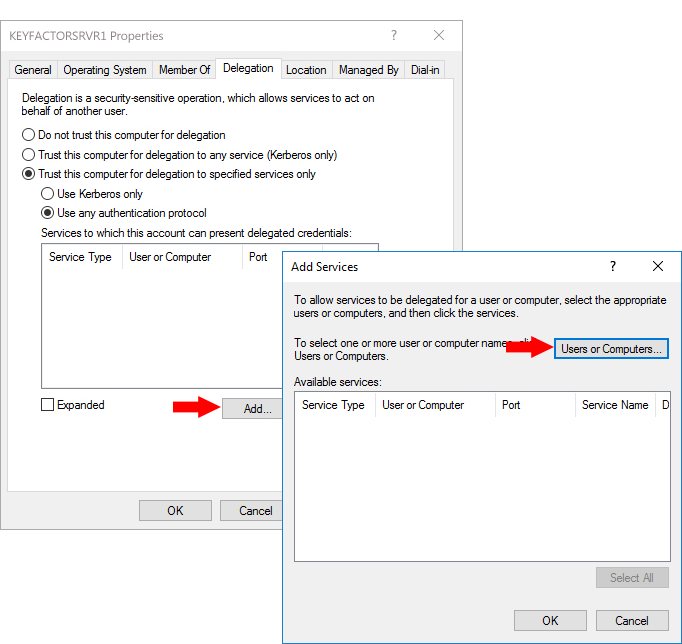
Figure 476: Configure Kerberos Constrained Delegation on the Keyfactor Command Machine Account
- In the Add Services dialog once the available services have populated, highlight both the HOST and the rpcss services (hold down the CTRL key when clicking the second service to select both at the same time) and click OK.
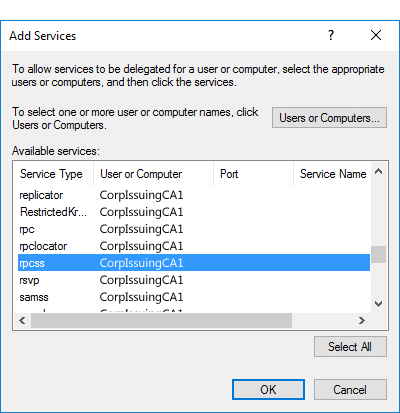
Figure 477: Add HOST and rpcss Service Types for Kerberos Constrained Delegation
- Back on the Delegation tab of the machine account Properties, you should see the HOST and rpcss services populate the "Services to which this account can present delegated credentials box". The server names do not appear as fully qualified domain names until you close the properties dialog and open it again.
- Repeat steps 3 and 4 for any other CAs to which you wish to delegate and then click OK.
To configure Kerberos constrained delegation on the service account under which the Keyfactor Command application pool is running:
- Open Active Directory Users and Computers and browse to locate the service account under which the Keyfactor Command application pool is running and open its properties.
- On the Delegation tab for the service account, choose "Trust the computer for delegation to specified services only" and under that "Use Kerberos only" and then click Add.
Important: This is a different configuration setting than for the machine account.Tip: The Delegation tab only appears on the properties sheet after you have configured a custom SPN.
- In the Add Services dialog, click Users or Computers and browse to locate the computer account for one of the CAs to which you wish to delegate.
- In the Add Services dialog once the available services have populated, highlight both the HOST and the rpcss services (hold down the CTRL key when clicking the second service to select both at the same time) and click OK.
- Back on the Delegation tab of the service account Properties, you should see the HOST and rpcss services populate the "Services to which this account can present delegated credentials box". The server names do not appear as fully qualified domain names until you close the properties dialog and open it again.
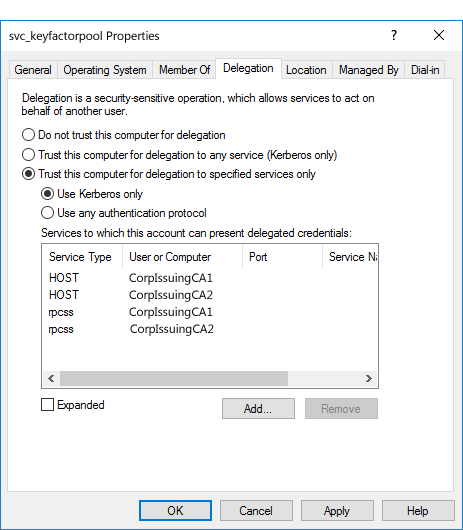
Figure 478: Configure Kerberos Constrained Delegation on the Keyfactor Command Service Account
- Repeat steps 3 and 4 for any other CAs to which you wish to delegate and then click OK.
To configure Kerberos resource-based constrained delegation:
- Create at least one Active Directory security group that will be used for granting delegation permission.Tip: The type of group to use and domain to place it in will vary depending on your forest
 An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. structure and the location of the accounts and resources in the forest. If your Keyfactor Command server(s), CA(s) and application pool service account are all in the same domain, any type of group in that same domain will do. If your Keyfactor Command server(s), CA(s) and/or application pool service account are separated across multiple domains, it becomes more complicated. If you add one or more cross-forest trusts into the mix that you want to do delegation across, that adds another level of complexity. Universal groups cannot be used in a cross-forest scenario, as they are not supported cross-forest. Some possible scenarios include:
An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. structure and the location of the accounts and resources in the forest. If your Keyfactor Command server(s), CA(s) and application pool service account are all in the same domain, any type of group in that same domain will do. If your Keyfactor Command server(s), CA(s) and/or application pool service account are separated across multiple domains, it becomes more complicated. If you add one or more cross-forest trusts into the mix that you want to do delegation across, that adds another level of complexity. Universal groups cannot be used in a cross-forest scenario, as they are not supported cross-forest. Some possible scenarios include:- All components (Keyfactor Command server(s), CA(s) and application pool service account) in the same domain: Create a group of any type in the same domain as these components.
- Keyfactor Command server(s) and application pool service account in child domain A and all CAs in the parent domain or child domain B with no cross-forest involvement: Create a universal group in the domain with the CAs (the parent domain or child domain B).
- Keyfactor Command server(s), application pool service account and CA(s) for forest A in the same domain, CAs in a single domain in forest B, forests A and B in a two way trust: Create a group of any type in the forest A domain where the Keyfactor Command server(s) reside and a group of type domain local in the forest B domain where the CAs reside; follow the below instructions for both domains and groups.
- Add the service account under which the Keyfactor Command application pool runs to this new security group.
- Add the machine account for the Keyfactor Command server to this new security group. Repeat for additional Keyfactor Command servers.
- On an Active Directory domain controller running Windows Server 2012 or better, open a PowerShell window using the "Run as administrator" option. If you're in a multi-domain or cross-forest environment, use a domain controller in the resource domain where the CAs exist.
- In the PowerShell window, run the following commands, where KerberosDelegationGroup is the name of your group for Kerberos delegation and IssuingCA is the machine name (no trailing $) of the CA you wish to delegate to:$mygroup = Get-ADGroup -Identity KerberosDelegationGroup
Set-ADComputer IssuingCA -PrincipalsAllowedToDelegateToAccount $mygroup - Repeat the Set-ADComputer step for any additional CAs.
- In the PowerShell window, run the following command for each CA to confirm that the group has been associated with the PrincipalsAllowedToDelegateToAccount property on the CA account:Get-ADComputer IssuingCA -Properties PrincipalsAllowedToDelegateToAccount

